Not all Open-source Software is Created Equal: Many Fail to Meet Integrity Standards, Leaving Organizations Open to Cyberattacks
Not all Open-source Software is Created Equal: Many Fail to Meet Integrity Standards, Leaving Organizations Open to Cyberattacks
New research from Lineaje assesses open-source software
SARATOGA, Calif.--(BUSINESS WIRE)--Lineaje, a leader in software supply chain security management, today released its new research report titled “What’s in Your Open-Source Software?” Compiled by the company’s research arm, Lineaje Data Labs, the report is a data-driven analysis into the integrity and reliability of open-source software (OSS), which now constitutes over 70% of all software. Focusing on the Apache Software Foundation as the gold standard of open-source software, the report uncovers the inherent risk and ease of software supply chain tampers in its most popular products and their dependencies. This inaugural installment of a series provides valuable insights into the often-opaque domain of OSS, shedding light on its integrity and implications for organizations’ security.
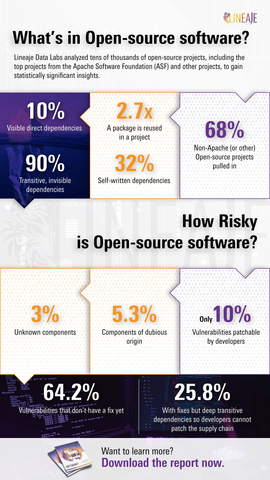
Lineaje Data Labs analyzed 41,989 open-source components embedded in the top 44 popular projects of the Apache Software Foundation across its last three versions. The analysis revealed that 68% of dependencies are on non-Apache Software Foundation open-source projects. These dependencies make even Apache Software Foundation’s integrity and inherent risk only as strong as the weakest component it embeds. With direct dependencies accounting for only 10%, the remaining 90% are transitive dependencies, which are not easily visible to developers selecting these packages. This creates an opaque and deep software supply chain invisible to developers.
“It's fascinating to note that although Apache is a large contributor to open-source software, a good portion of the software it relies on is non-Apache Software Foundation. This highlights the incredible diversity and complexity of the open-source community,” said Manish Gaur, Head of Product Security at VMware after reviewing the research report.
The research reveals some additional insights about open-source software risk:
- Extremely high inherent risk – 82% of components are inherently risky due to vulnerabilities, security issues, code quality or maintainability concerns.
- Popularity of software does not indicate quality – Thus, choosing dependencies based on their popularity is not a reliable risk mitigation approach. Apache Software Foundation’s eCharts is its most popular package and is also one of the riskiest, for example.
- The mirage of patching vulnerabilities – While organizations drown in a sea of patches they must apply, the research uncovers that 64.2% of all vulnerabilities have no fixes available yet — so they cannot be patched. At the same time, due to the deep transitive nature of dependencies, another 25.8% of all vulnerabilities are not patchable by the organization deploying or including open-source software. Effectively, complete patching — if achieved — addresses only about 10% of the vulnerability exposure of an organization.
It is crucial to note that the most significant risk lies not in the vulnerabilities that are not patched, but in those for which no fixes exist. These vulnerabilities continue to exist and pose a persistent threat, regardless of other patches applied.
The ability to detect tampering of the software supply chain is directly linked to software integrity. Of the tens of thousands of open-source projects decomposed by Lineaje Data Labs, results showed:
- Unknown components – While the majority of software assessed had high integrity attestable components, our research reveals that about 3% of all components had no known origin. These are deeply embedded in Apache Software Foundation software, and their origin and update mechanisms are opaque.
- Dubious origin components – 5.3% of components failed a basic integrity check that the package published by developers matched the source code it claimed to be associated with. This kind of integrity check would have flagged both the recent 3CX compromise as well as the SolarWinds compromise.
“It’s imperative that organizations today understand that open-source software has risks and is tamper-able, even if it is very popular or provided by an established brand,” said Lineaje CEO and Co-founder Javed Hasan. “With more software being assembled than built, it’s become more important than ever to have formal tools to discover software DNA. Developers do not have X-ray vision to see inside a software component they include nor are most open-source selectors security experts. We must use software supply chain management tools like SBOM360 to continuously assess the dynamic, inherent risk and integrity of these software components that are built left of shift-left.”
Additional resources
- Read the complete findings from the “What’s in Your Open-Source Software?” report.
- Schedule a consultation with Lineaje to learn more about SBOM360, the first-of-a-kind software supply chain management solution.
- Visiting RSA Conference 2023? Come see us at Southside Spirit House on Monday, April 25 and Tuesday, April 26.
To learn more about how Lineaje’s flagship product SBOM360 can help assess open-source software and attest to its integrity, visit https://www.lineaje.dev/products/SBOM360.
About Lineaje
Lineaje provides Continuous Software Supply Chain Security Management to companies that build or use software. Destructive supply chain attacks, undetectable by existing cybersecurity tools, are growing rapidly, impacting thousands of companies through a single compromise. Lineaje secures companies from these attacks. Lineaje SBOM360 allows companies to centrally manage their entire software supply chain, which consists of applications they build or buy, thereby allowing them to govern SBOMs at an enterprise-wide level. SBOM360 also enables compliance with US Executive order 14028 and other international regulations that control the procurement of third-party software by federal agencies, defense departments and other government organizations.
Does your organization know ‘what’s in its software?’ Find out at https://www.lineaje.com/
Contacts
Touchdown PR
Alyssa Pallotti
lineaje@touchdownpr.com