SARATOGA, Calif.--(BUSINESS WIRE)--Lineaje, a leader in software supply chain security management, today released a comprehensive report that identified the U.S. and Russia as the top generators of open-source projects – with the highest numbers of anonymous open-source contributions to match. The study, “Crossing Boundaries: Breaking Trust,” delivers a stark assessment of global software supply chains, revealing where the deepest layers of open-source software component dependencies originate from and their critical vulnerabilities. Compiled by the company’s research arm, Lineaje AI Labs, it includes analysis from its open-source dependency crawlers, which continuously assess more than 7 million open-source packages.
Open Source’s Global Nature Exposes Software to Geopolitical Risks
The geographic distribution of open-source contributions introduces geopolitical risks that organizations must urgently consider, especially with rising nation-state attacks. Microsoft estimates that its customers face 600 million cyberattacks daily, 24% of which are nation-state attackers targeting the IT sector. With software supporting increasingly vital systems, the origin of code has become a matter of national and economic security.
The findings revealed that for a typical mid-sized application:
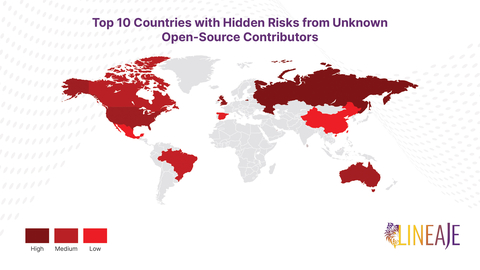
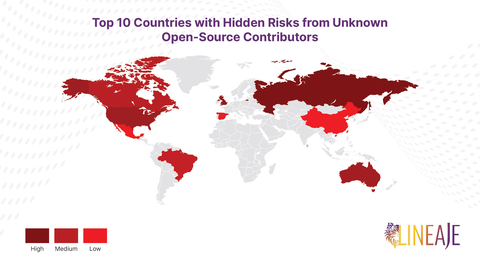
- The U.S. Contributes More Code to Open-Source Projects Than Any Other Country: More than one-third (34%) of open-source contributions come from the U.S., 13% from Russia, and smaller percentages from Canada, the U.K., and China.
- The U.S. Has the Highest Percentage of Anonymous Open-Source Contributors: Of the U.S. open-source contributions, 20% are anonymous — more than twice the rate of its Russian counterparts and three times that of Chinese contributors. Globally, 5-8% of all open-source components of any application are unknown, tampered with, or of dubious origin - many of which are contributed anonymously. The implication is that developers are incorporating code into projects without fully understanding its lineage and functionality, potentially introducing hidden backdoors, malware, or critical vulnerabilities and posing significant risks.
- Geo-Provenance Concerns Are Most Acute in Critical Software: Vital industries such as defense systems, water, electricity, banking, and retail struggle with software maintenance. Because these industries often have contributors from multiple countries, excluding any adversarial nations completely is challenging.
Worldwide, Open Source Has Major Maintenance Gaps
The Lineaje report revealed that regardless of geographic origin, the average mid-size application has several disturbing trends leading to critical vulnerabilities, including:
- Open Source is Driving Security Weaknesses: Open source contributes 2 to 9 times the code your developers write, and over 95% of security weaknesses originate within open-source package dependencies. Over half (51%) of these vulnerabilities, across all CVE severity levels, have no known fixes. Additionally, 70% of open-source components are no longer maintained or poorly maintained.
- Unmaintained Open Source is Less Vulnerable: Surprisingly, unmaintained open source is less vulnerable than well-maintained open-source, which is 1.8 times more vulnerable. The high rate of change in well-maintained components enhances risks.
- Vulnerabilities Lurk in the Deepest Layers, and Fixing Them is Challenging: Individual open-source projects embed up to 60 layers of components from dozens of open-source organizations. They are often assembled in a complex Lego structure in a single dependency that developers include in their organizations' applications, leading to poor risk assessment and even poorer remediation approaches. Knowing which vulnerabilities developers can fix easily and which they should not, eliminates at least 50% of the vulnerability fix effort and improves security posture by 20-70%.
- Version Sprawl is Causing Complications: More than 15% of open-source components have multiple versions in a single application, making remediation efforts more difficult.
- Coding Language Diversity is Introducing Security Risks: A mid-sized application can pull in 1.4 million lines of code across 139 languages and often drags in more risky memory-unsafe languages. Secure-by-design organizations may use memory-safe languages in private code, but their dependencies exacerbate security risks unless language is a selection criterion for open-source dependencies.
- Team Size Impacts Quality and Security: Open-source projects staffed by very small teams (<10) and large teams (>50) deliver more risky packages than mid-sized teams. Small teams deliver 330% more risky projects than mid-sized teams, while larger teams deliver packages with 40% more risk than mid-sized teams.
“Open-source software is a complex web of dependencies originating from around the world, often extending 30 levels deep or more. This latest Lineaje AI Labs research proves that organizations are completely blind when it comes to understanding the true composition of their open-source code and its origins, putting them at serious risk,” said Javed Hasan, CEO and co-founder, Lineaje. “Amidst current geopolitical tensions and global dependency on open-source code, it’s critical for enterprises to equip themselves with robust software supply chain security and maintenance tools that uncover hidden security gaps and provide a comprehensive, real-time view of potential vulnerabilities – while ensuring compliance with ever-evolving standards.”
“Open-source projects enable industry-transforming product innovation for entrepreneurs, government agencies, and companies around the world. However, with great innovation comes even greater risks – but that doesn’t mean the risks aren’t worth taking,” said Manish Gaur, Director, Product Security VMWare by Broadcom. “Lineaje AI Labs’ report provides valuable insights on what open-source-driven threats and trends we, as software creators, must keep an eye on – and what we must do to protect our code, our customers, and our companies.”
Additional Resources
- Read the complete findings from the “Crossing Boundaries: Breaking Trust” report.
- Schedule a consultation with Lineaje to learn more about its comprehensive security and governance platform.
To stay up-to-date on open-source software security research, visit https://www.lineaje.com and follow Lineaje’s LinkedIn page.
About Lineaje
Lineaje provides Continuous Software Supply Chain Security Management to companies that build or use software. Destructive supply chain attacks, undetectable by existing cybersecurity tools, are growing rapidly, impacting thousands of companies through a single compromise. Lineaje secures companies from these attacks. Lineaje SBOM360 allows companies to centrally manage their entire software supply chain, which consists of applications they build or buy, thereby allowing them to govern SBOMs at an enterprise-wide level. SBOM360 also enables compliance with US Executive Order 14028 and other international regulations that control the procurement of third-party software by federal agencies, defense departments and other government organizations.
Does your organization know ‘what’s in its software?’ Find out at https://www.lineaje.com.