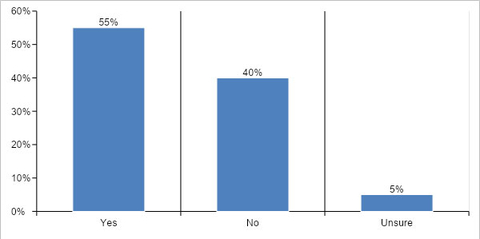
PALO ALTO, Calif.--(BUSINESS WIRE)--55% of respondents indicated that they had a cybersecurity incident because an available patch was not applied, according to a report released today by TuxCare showing the heavy burden on companies due to a wide range of cyberattacks. Data from respondents in IT and IT security fields shows that companies take too long to patch security vulnerabilities, even when solutions already exist.
Main Takeaways
- Patching is one of the most important steps an organization can take to protect themselves from ransomware and other cyberattacks
- Patching vulnerabilities is not just limited to the kernel, it needs to extend to other systems like libraries, virtualization and database back ends
- Automation can take the pain out of patching
“Our research with TuxCare reveals the issues organizations have with achieving the timely patching of vulnerabilities despite spending an average of $3.5 million annually and 1,075 hours weekly monitoring systems for threats and vulnerabilities, patching, documenting and reporting the results,” said Dr. Larry Ponemon, chairman and founder of Ponemon Institute. “To address this problem, CIOs and IT security leaders need to work with other members of the executive team and board members to ensure security teams have the resources and expertise to detect vulnerabilities, prevent threats and patch vulnerabilities in a timely manner.”
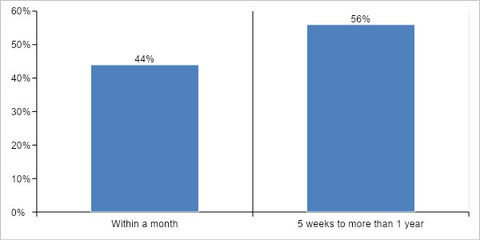
Over 55% of cybersecurity incidents occurred when a patch was readily available. Organizations take too long to fix security vulnerabilities. 56% of respondents take 5 weeks to 1 year to fix critical or high priority security vulnerabilities.
“The data shows that companies simply take too long to address vulnerabilities. This is a fixable issue. It is not because the solution does not exist, it is because it is hard to prioritize future problems,” said Igor Seletskiy, CEO and founder of TuxCare. "One possibility for improving these numbers is live patching. Live patching is a technology solution that can make a difference immediately. It is rebootless and reduces patching tasks by as much as 60%. More importantly, live patching shrinks risk timeframes by greatly accelerating patch cycles."
Live patching is the process of deploying carefully prepared and extensively tested patches to critical components like the kernel, shared libraries, and databases while the server is still running, updating it automatically. Patches can be applied without delay or downtime since there is no need to wait for restarting systems and services.
The report’s goal was to understand how organizations are managing security and stability in the Linux suite of products. Sponsored by TuxCare, the Ponemon Institute surveyed 564 IT and IT security practitioners in 16 different industries in the United States. The results were published in February 2022.
To download the full report, go here.
About TuxCare
TuxCare provides security solutions to thousands of customers, including Zoom, IBM, Dell, Mitre, Datto and Proofpoint. We offer a full suite of live patching and support services for all popular Linux distributions to help organizations maintain a compliant and secure posture against cybersecurity risks. For more information, go to TuxCare.com.