SAN FRANCISCO--(BUSINESS WIRE)--Cycode, an innovator in securing DevOps pipelines, today announced a $20 million Series A round led by Insight Partners, with participation from seed investor, YL Ventures. The new funding brings total investment to $25 million and positions Cycode to accelerate growth into securing enterprise DevOps tools such as source control management systems, build systems and cloud infrastructure.
In addition to the Series A funding, Cycode also announced the signing of new customers including: Grubhub, Databricks, Flexport, Rapyd, Copart and Cobalt. Further, Cycode has hired Dor Atias as VP of R&D, Tom Kennedy as VP of Sales and Andrew Fife as VP of Marketing.
As the Software Development Lifecycle (SDLC) has become faster and more automated, slow application security processes have often been deprioritized in favor of new feature velocity. Additionally, many of the new tools that drive the automation and efficiency in application development have opened up new attack surfaces and created new security challenges. The adoption of Everything as Code means attacks no longer have to start in production. In development, gaining access to source control management systems enables code tampering, finding passwords to critical systems and modifying cloud configurations (through code) to allow unauthorized access.
“Modernizing the SDLC has created new security gaps that attackers are readily exploiting,” said Ronen Slavin, CTO and co-founder of Cycode. “Recent supply chain attacks like SolarWinds and Codecov, major source code leaks from Microsoft and Nissan, and attacks targeting developers like Sawfish and XcodeSpy demonstrate that the battlefield is already shifting.”
Cycode protects DevOps tools such as source control management systems, build systems, registries and cloud infrastructure. The solution addresses multiple layers of security, including access and authorization, security configurations, compliance and scanning engines. This enables customers to identify code tampering, code leakage, hardcoded secrets, Infrastructure as Code (IaC) misconfigurations, excess privileges and more, all from a single platform.
To ensure customers never have to choose between security and speed, Cycode provides workflows to automate remediation. Customers can also seamlessly integrate remediation into their developers’ workflows via pre-built integrations with pull requests, alerting and ticketing systems.
“As the leading Pentest as a Service company, our internal security has always been paramount,” said Ray Espinoza, CISO at Cobalt. “Cycode has saved us a massive number of hours hardening our source control management system, enforcing security configurations and preventing secrets from entering our code. Plus, by plugging seamlessly into our developers’ workflows, our team adopted Cycode right away.”
Today, Cycode launches its knowledge graph to derive security insights from the rapidly increasing volumes of data and alerts that are overwhelming security teams. Through an agentless architecture, Cycode collects asset information and user activity from DevOps tools, infrastructure and security scanners, which is then mapped in its knowledge graph. By correlating events across the SDLC, Cycode’s knowledge graph creates contextual insights, helps prioritize remediation, reduces false positives and ensures the integrity of the pipeline to prevent code tampering incidents, such as the breaches at SolarWinds and Codecov.
“The problem of protecting CI/CD tools like GitHub, Jenkins and AWS is a gap for virtually every enterprise,” said Jon Rosenbaum, principal at Insight Partners, who will join Cycode’s board of directors. “Cycode secures CI/CD pipelines in an elegant, developer-centric manner. This positions the company to be a leader within the new breed of application security companies -- those that are rapidly expanding the market with solutions which secure every release without sacrificing velocity.”
“With these new funds, part of the focus will naturally be on expanding sales and marketing efforts,” said Lior Levy, CEO and co-founder of Cycode. “What I’m really excited about is expanding Cycode’s platform with even more integrations into CI/CD and security tools to increase the power of our knowledge graph. Furthermore, we’re releasing a low-code query engine and a knowledge-sharing community that will enable security teams without development expertise to leverage the full power of the graph.”
About Cycode
Cycode secures DevOps pipelines and provides full visibility into enterprise development infrastructure. Powered by its knowledge graph, Cycode’s advanced detection capabilities correlate event data and user activity across the SDLC to create contextual insights and automate remediation. Cycode delivers security, governance and pipeline integrity without disrupting developers’ velocity.
About Insight Partners
Insight Partners is a leading global venture capital and private equity firm investing in high-growth technology and software ScaleUp companies that are driving transformative change in their industries. Founded in 1995, Insight Partners has invested in more than 400 companies worldwide and has raised through a series of funds more than $30 billion in capital commitments. Insight’s mission is to find, fund and work successfully with visionary executives, providing them with practical, hands-on software expertise to foster long-term success. Across its people and its portfolio, Insight encourages a culture around a belief that ScaleUp companies and growth create opportunity for all. For more information on Insight and all its investments, visit insightpartners.com or follow us on Twitter @insightpartners.
About YL Ventures
YL Ventures funds and supports brilliant Israeli tech entrepreneurs from seed to lead. Based in Silicon Valley and Tel Aviv, YL Ventures manages over $300 million and specializes in cybersecurity. YL Ventures accelerates the evolution of portfolio companies via strategic advice and U.S.-based operational execution, leveraging a powerful network of Chief Information Security Officers and global industry leaders. The firm's track record includes successful, high-profile portfolio company acquisitions by major corporations including Palo Alto Networks, Microsoft, CA and Proofpoint.
Heading the fund is Silicon Valley-based Managing Partner Yoav Andrew Leitersdorf, a serial entrepreneur and early-stage investor for over 25 years. Yoav works alongside Partner John Brennan in the U.S., while Partner & Head of Israeli Office Ofer Schreiber leads the Tel Aviv office together with Chief Marketing Officer Sharon Seemann. With a multidisciplinary team of 15 spread across two offices, YL Ventures has engrained itself in both the U.S. and Israeli cybersecurity ecosystems. For more information, visit ylventures.com.
ADDENDUM FOR JOURNALISTS
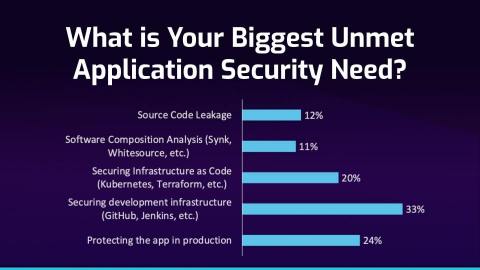
AppSec’s Biggest Unmet Need
91 respondents | Poll Completed in April 2021
See “Figure 1: Poll findings” in multimedia resources
Cycode Knowledge Graph
Example Use Cases
Uncover issues that require comparison across the SDLC:
- Code in the SCM doesn’t match code in build systems, which is how SolarWinds’ code was tampered with
- Shell script in the main branch doesn’t match the file in the storage bucket, which is how Codecov’s code was tampered with
- Production container images that weren’t pulled from an authorized registry
- Images in a public package registry expose code from a private repository
- Drift between IaC configurations and production settings
Answer complex questions in a simple manner:
- Which commits created a particular artifact?
- Which users have access both to production and CI/CD?
- Which storage buckets hold build outputs like artifacts, code, scripts, etc.?
- What is the activity (commits, clones, downloads, etc.) of employees leaving in the next 30 days?
- Custom questions that are unique to a specific environment
Prioritize vulnerabilities and reduce false positives:
- Dependency vulnerability identified in development that is not reachable in production
- SQL Injection vulnerabilities in custom code found in dev that is protected by custom sanitization steps in production
- Secrets detected in version history, or build logs, that are no longer active in production
The Attack Surface Has Shifted
Recent DevOps Pipeline Tools & Infrastructure Incidents
- April 24th, 2021: Click Studios informs its customers that Click Studios’ password manager had been compromised and used as a supply chain attack vector
- April 20th, 2021: Hundreds of Codecov customers are breached in supply chain attack
- March 18th, 2021: XcodeSpy malware targets developers with a remote access trojan
- March 29th, 2021: PHP’s Git server was hacked to add backdoors into PHP’s source code
- Jan 7th, 2021: Nissan leaks source code by failing to change a default password on a Bitbucket server
- Dec 23rd, 2020: Accellion notifies their customers that Accellion had been compromised and used as a supply chain attack vector
- Dec 13th, 2020: FireEye announces that it has been compromised via the previously unknown SolarWinds supply chain attack
- September 30th, 2020: Microsoft Leaks Key Operating System Source Code (XP & More)
- May 28th, 2020: The Octopus Scanner malware targets GitHub
- May 18th, 2020: Mercedes leaks OLU source code online
- April 4th, 2020: The Sawfish attack targets developers’ GitHub accounts
- Jan 2nd, 2020: Starbucks exposes API key in public GitHub Repository