WOBURN, Mass.--(BUSINESS WIRE)--Kaspersky Lab released its report on the Industrial Control Systems (ICS) threat landscape, which revealed that large organizations likely have ICS components connected to the internet that could allow cybercriminals to attack critical infrastructure systems.
The investigation found that 17,042 ICS components on 13,698 different hosts exposed to the Internet, likely belong to large organizations. These organizations include energy, transportation, aerospace, oil and gas, chemicals, automotive and manufacturing, food and service, governmental, financial and medical institutions.
To minimize the possibility of a cyber-attack, ICS should be run in a physically isolated environment; however, the report shows that thousands of hosts are being exposed with 91.1 percent of these ICS hosts having vulnerabilities that can be exploited remotely. In addition, 3.3 percent of ICS hosts located in these organizations contain critical vulnerabilities that can be exploited remotely.
Connected systems are more flexible, able to react quickly to critical situations and implement updates, but in turn, this gives cybercriminals a chance to remotely control critical ICS components. This can result in physical harm to the equipment as well as potential danger to the whole critical infrastructure.
The major findings of the Industrial Control Systems Threats Landscape report are:
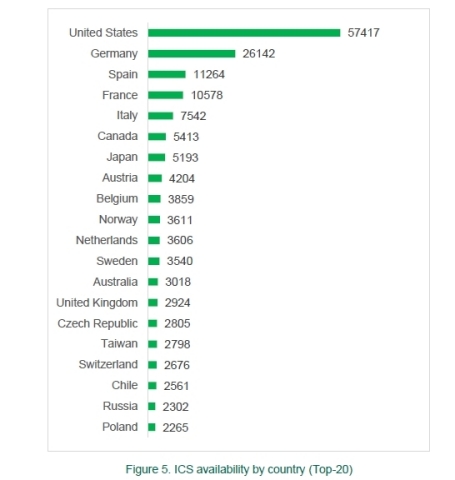
- In total, 188,019 hosts with ICS components available via the Internet have been identified in 170 countries.
- Most of the remotely available hosts with ICS components installed are located in the United States of America (30.5 percent - 57,417) and Europe. In Europe, Germany has a leading position (13.9 percent - 26,142 hosts), followed by Spain (5.9 percent - 11,264 hosts), and France (5.6 percent - 10,578 hosts).
- 92 percent (172,982) of remotely available ICS hosts have vulnerabilities. 87 percent of these hosts contain medium risk vulnerabilities and 7 percent of them have critical vulnerabilities.
- The number of vulnerabilities in ICS components has increased tenfold during the past five years: from 19 vulnerabilities in 2010 to 189 vulnerabilities in 2015. The most vulnerable ICS components were Human Machine Interfaces (HMI), Electric Devices and SCADA systems.
- 91.6 percent (172,338 different hosts) of all the externally available ICS devices use weak Internet connection protocols, which opens the opportunity for attackers to conduct ’man in the middle’ attacks.
“There is no 100 percent guarantee that a particular ICS installation won’t have at least one vulnerable component at any single moment in time,” said Andrey Suvorov, Head of Critical Infrastructure Protection, Kaspersky Lab. “However, this doesn’t mean that there is no way to protect a factory, a power plant, or even a block in a smart city from cyber-attacks. Simple awareness of vulnerabilities in the components used inside a particular industrial facility is the basic requirement for security management of the facility.”
To help organizations working with ICS to identify their possible weak points, Kaspersky Lab experts conducted an investigation into ICS threats which resulted in the Industrial Control Systems Threat Landscape report. The analysis was based on OSINT (Open Source Intelligence) and information from public sources like ICS CERT, with the research period limited to 2015.
To read the full Industrial Control Systems Threat Landscape report, please visit Securelist.com.
About Kaspersky Lab
Kaspersky Lab is a global cybersecurity company founded in 1997. Kaspersky Lab’s deep threat intelligence and security expertise is constantly transforming into security solutions and services to protect businesses, critical infrastructure, governments and consumers around the globe. The company’s comprehensive security portfolio includes leading endpoint protection and a number of specialized security solutions and services to fight sophisticated and evolving digital threats. Over 400 million users are protected by Kaspersky Lab technologies and we help 270,000 corporate clients protect what matters most to them.
Learn more at www.kaspersky.com.
For the latest in-depth information on security threat issues and
trends, please visit:
Securelist
| Information about Viruses, Hackers and Spam
Follow @Securelist on
Twitter
Threatpost
| The First Stop for Security News
Follow @Threatpost on
Twitter