PORTLAND, Ore.--(BUSINESS WIRE)--Tripwire, Inc., a leading global provider of advanced threat, security and compliance solutions, today announced an analysis of Microsoft patch data from 2014. Supplementary trend data dating back to 2009 was collected, categorized and analyzed by Tripwire’s Vulnerability and Exposure Research Team (VERT). Additional details and charts can be found here: http://www.tripwire.com/vert/2014-microsoft-patch-tuesday-trend-data/.
“The 2014 data clearly shows that Microsoft is packing in more CVEs per bulletin in 2014,” said Lane Thanes, security researcher for Tripwire. “One contributing factor to this change is the growing base of security researchers who disclose Microsoft vulnerabilities, and another factor is the improved research tools researchers have access to that allow them to discover vulnerabilities faster.”
Key findings from Tripwire’s 2014 Microsoft patch analysis include:
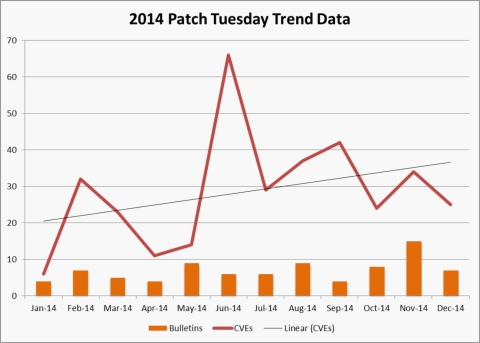
- The average number of Common Vulnerability Exposures (CVEs) per month did not increase or decrease from 2013 to 2014. However, after a slow start in the beginning of the year, CVEs increased by 20 percent in the second half of 2014.
- There were 28 critical bulletins in 2014 – down from 42 in 2013. Internet Explorer (IE) made up 43 percent of 2014’s critical vulnerabilities. There has not been a noncritical IE update since December 2011.
- There were 12 IE updates in 2014 – down from 14 in 2013.
- The average number of bulletins per month decreased from nine to seven between 2013 and 2014.
Thanes has two predictions for 2015 patches: “First, I don’t foresee an abrupt change in the CVE per bulletin density over the next year. It is likely that Microsoft will continue to pack a lot of CVEs into every bulletin, and the majority of this density will likely be due to Internet Explorer. Second, it’s possible that we will see an uptick in the number of out-of-band Microsoft security bulletins due to Google’s Project Zero. On average, Microsoft will only have 70 to 80 days to fix, test and deliver patches for vulnerabilities discovered by Project Zero, given the fixed Patch Tuesday cycle and Project Zero’s rigid 90-day time frame.”
Microsoft releases the newest security fixes for its Windows operating system and related software applications on the second Tuesday of each month. The majority of these Microsoft patches are sent out on “Patch Tuesday,” although code fixes deemed critical may be sent at any time. System administrators and IT security teams are then able to plan for the security updates and allocate necessary resources to keep critical systems patched.
“It’s interesting that there was such a massive drop in critical patches from 2013 to 2014,” said Craig Young, security researcher for Tripwire. “Windows XP wound down in April 2014, but I don’t see any drop-off in the trend data specific to its end of life. Dropping Windows XP support could have led to the reduced number of critical bulletins due to the improved security measures of newer versions. However, it’s possible that the overall bulletins did not decrease because a lot of Windows XP code continues to be used in Microsoft’s newer systems.”
About Tripwire
Tripwire is a leading provider of advanced threat, security and compliance solutions that enable enterprises, service providers and government agencies to confidently detect, prevent and respond to cybersecurity threats. Tripwire solutions are based on high-fidelity asset visibility and deep endpoint intelligence combined with business-context and enable security automation through enterprise integration. Tripwire’s portfolio of enterprise-class security solutions includes configuration and policy management, file integrity monitoring, vulnerability management and log intelligence. Learn more at www.tripwire.com, get security news, trends and insights at http://www.tripwire.com/state-of-security/ or follow us on Twitter @TripwireInc.